Difference between revisions of "Integrity Check"
From Contao Community Documentation
m |
|||
| (44 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
'''''I'm not a native English speaker. Please correct my mistakes.''''' | '''''I'm not a native English speaker. Please correct my mistakes.''''' | ||
<br /><br /> | <br /><br /> | ||
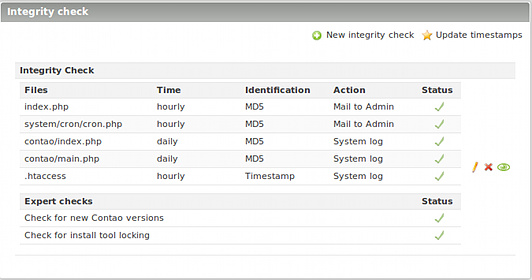
| − | Integrity check for some files from Contao (Detection of hacked Contao installations.) | + | [[File:check_overview_en.jpg|right|Integrity Check]] Integrity check for some files from Contao (Detection of hacked Contao installations.) |
{{ExtInfo | {{ExtInfo | ||
| Dev=Glen Langer ([[User:BugBuster|BugBuster]]) | | Dev=Glen Langer ([[User:BugBuster|BugBuster]]) | ||
| DevSite=http://www.contao.glen-langer.de | | DevSite=http://www.contao.glen-langer.de | ||
| − | | ExtVersion= | + | | ExtVersion=1.3.10 / 3.4.0 |
| − | | Version= | + | | Version=from 2.10.0 |
| ERLink=http://www.contao.org/en/extension-list/view/integrity_check.en.html | | ERLink=http://www.contao.org/en/extension-list/view/integrity_check.en.html | ||
| TrackerLink=https://github.com/BugBuster1701/integrity_check/issues | | TrackerLink=https://github.com/BugBuster1701/integrity_check/issues | ||
| Line 20: | Line 20: | ||
Questions about the Bot Detection module will be answered in [http://www.contao-community.org/viewforum.php?f=21 Forum]<br /> | Questions about the Bot Detection module will be answered in [http://www.contao-community.org/viewforum.php?f=21 Forum]<br /> | ||
Errors and requests can be reported in the [https://github.com/BugBuster1701/integrity_check/issues Issue Tracker]. | Errors and requests can be reported in the [https://github.com/BugBuster1701/integrity_check/issues Issue Tracker]. | ||
| + | |||
| + | =Translations= | ||
| + | Translations can be performed on [https://www.transifex.com/projects/p/contao-integrity_check/ Transifex] | ||
=Installation= | =Installation= | ||
| Line 35: | Line 38: | ||
#/c3284d# | #/c3284d# | ||
</source> | </source> | ||
| + | |||
| + | Or like this (shortened):<br /> | ||
| + | <source lang="javascript"> | ||
| + | <script type="text/javascript"> | ||
| + | function frmAdd() { | ||
| + | var ifrm = document.createElement('iframe'); | ||
| + | .... | ||
| + | }; | ||
| + | window.onload = frmAdd; | ||
| + | </script> | ||
| + | </source> | ||
| + | |||
| + | ==Site one the black list== | ||
| + | When you does not react fast enough, and Google notices this, the page is set to the "black list". Browsers like Firefox use this to warn against unauthorized access to it. It looks like this:<br /> | ||
| + | [[File:site_on_black_list_en.jpg]] | ||
=Function of the module= | =Function of the module= | ||
| − | In the current version | + | In the current version, the most important PHP files are checked for modifications.<br /> |
This files will be checked: | This files will be checked: | ||
* index.php | * index.php | ||
| + | * cron.php (from version 1.1.0) | ||
* contao/index.php | * contao/index.php | ||
* contao/main.php | * contao/main.php | ||
| + | * .htaccess (from version 3.1.0) | ||
| + | |||
| + | Special warning tests: | ||
| + | * Check for new Contao versions (from version 3.4.0) | ||
| + | * Check for install tool locking (from version 3.4.0) | ||
==Time of verification== | ==Time of verification== | ||
| − | This test is performed automatically | + | This test is performed automatically (Contao-Cron), see the section [[Integrity_Check#Technical_Details|Technical Details]]. |
==Detection== | ==Detection== | ||
| − | The check is identical to the official Contao check tool, that means via MD5 checksums. Checksums are available for comparison for Contao from 2.10.0. | + | The check is identical to the official Contao check tool, that means via MD5 checksums. Checksums are available for comparison for Contao from 2.10.0.<br /> |
| + | From version 1.1.0, check via timestamps is possible. | ||
==Using== | ==Using== | ||
| − | In the backend, you can see the results: System - System Log. Normally | + | In the backend, you can see the results: System - System Log. Normally if everything is OK, no message appears. In its own module debug mode then there is only a message:: |
| − | * | + | * Checking files for integrity is completed. |
If modifications were detected, a message is generated for each file: | If modifications were detected, a message is generated for each file: | ||
| − | * Integrity status for file index.php is: Corrupt | + | * Integrity status for file index.php is: Corrupt [MD5] |
| − | An information | + | * Integrity status for cron.php file is corrupted [Timestamp] |
| + | ** It was checked by time stamp, possible from version 1.1.0. | ||
| + | An information is available via System Log and mail, see the section [[Integrity_Check#Technical_Details|Technical Details]]. | ||
| − | = | + | =Technical Details= |
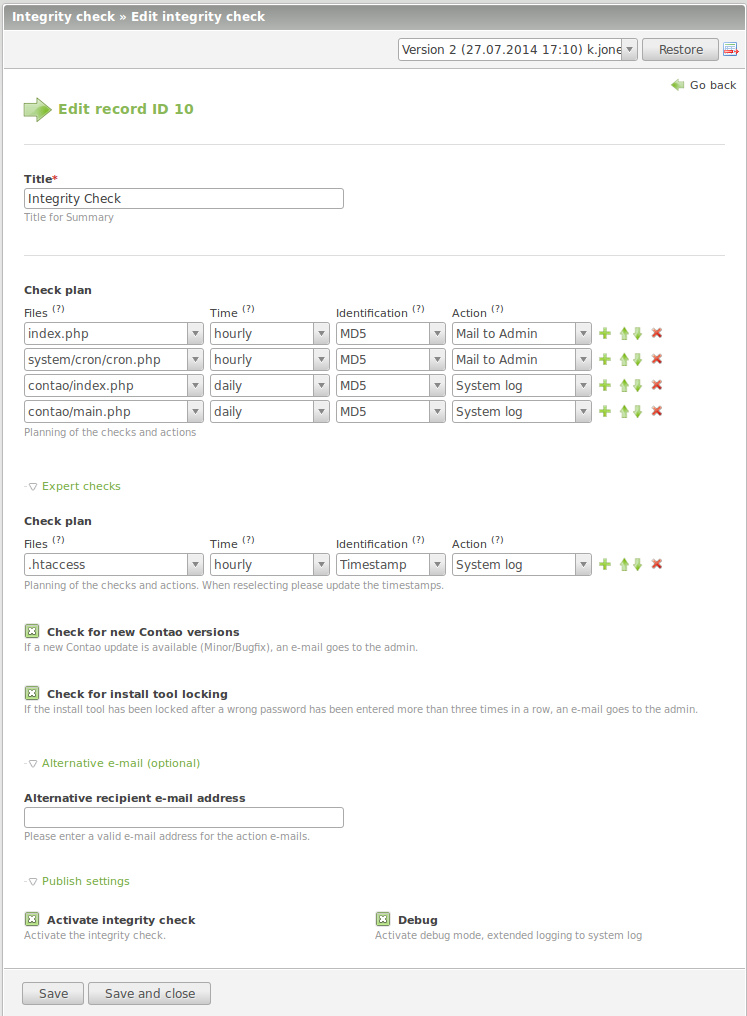
| − | == | + | ==Creating integrity check== |
| − | + | The integrity check need a check plan. This can be used for any of the files for the time, the art of check and the action.<br /> | |
| − | + | ||
| − | + | ||
| − | </ | + | |
| − | + | [[File:check_plan_en.jpg]] | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | == | + | ===Time intervals=== |
| − | + | * in Contao 2.10: daily, weekly, monthly | |
| − | + | * in Contao 2.11: hourly, daily, weekly, monthly | |
| − | + | * in Contao 3.0: minutely(manual), hourly, daily, weekly, monthly | |
| − | </ | + | |
| + | ===Art of check=== | ||
| + | The detection of a change in the file is possible via: | ||
| + | * MD5 checksum | ||
| + | * Timestamps | ||
| + | |||
| + | ===Action=== | ||
| + | * System log: Message in the system log (backend) | ||
| + | * Mail to Admin: a mail is sent to the admin of the Contao installation. | ||
| + | ** It will then creates also automatically an entry in the System log (from version 1.1.0) | ||
| + | |||
| + | ==Notes== | ||
| + | ===System-Log und Mail=== | ||
| + | From version 1.1.0 automatically gets an entry in the system log when a mail is sent.<br /> <br /> | ||
| + | In Version 1.0.0, if you want to have both types of information, you creates the check twice, each with one of the actions: <br /> | ||
| + | |||
| + | [[File:check_plan_2_en.jpg]] | ||
| + | <br /> | ||
| + | Here is an example only for the index.php. This is of course also for the other files. | ||
| + | |||
| + | ===There can be only one!=== | ||
| + | It is possible in the integrity check overview to create multiple checks. It basically makes no sense. Therefore, it is ensured that there can be only an integrity check, which is activated. If you switch a new integrity check active, all other existing tests are automatically switched inactive. | ||
| − | == | + | ==Protection against infection== |
| − | + | Well, a general protection is probably not possible.<br /> | |
| − | + | But there is a possibility that the malicious code is not executed. There is a ticket to GitHub, it is accepted for Contao 3. Here is the short info for Contao 2.<br /> | |
| − | + | Edit the index.php, go to the method "run" in the last line, should be the line of 269th (2.11.5) Before the curly bracket insert an exit; or insert a row for it. Here is from line 268 as an example: | |
<source lang="php"> | <source lang="php"> | ||
} | } | ||
} | } | ||
</source> | </source> | ||
| − | + | change to: | |
<source lang="php"> | <source lang="php"> | ||
} | } | ||
| Line 89: | Line 130: | ||
} | } | ||
</source> | </source> | ||
| − | + | Note: Now, the Integrity Check Tool as well as the Contao Check Tool report a change. Use the check vie timestamp now. | |
| − | + | ||
| + | |||
| + | |||
| + | ---- | ||
| + | --[[User:BugBuster|BugBuster]] ([[User talk:BugBuster|talk]]) 18:31, 27 July 2014 (CEST) | ||
Latest revision as of 17:31, 27 July 2014
I'm not a native English speaker. Please correct my mistakes.
| Extension-Overview | |
|---|---|
| Name of the developer | Glen Langer (BugBuster) |
| Developer Website | http://www.contao.glen-langer.de |
| Version of the extension | 1.3.10 / 3.4.0 |
| Compatibility with Contao Version | from 2.10.0 |
| Link to Extension Repository | http://www.contao.org/en/extension-list/view/integrity_check.en.html |
| Link to Tracker | https://github.com/BugBuster1701/integrity_check/issues |
In Contao Forum, reports came about changed files, which malicious code was attached.
The problem itself can not be attributed to a vulnerability in Contao, but will be distributed over other ways of the server, eg vulnerable WP plugins, hacked servers, hacked FTP logins, etc.
Contents
Forum
Questions about the Bot Detection module will be answered in Forum
Errors and requests can be reported in the Issue Tracker.
Translations
Translations can be performed on Transifex
Installation
The installation of the module occurs about the extension Repository in back end of Contao.
A manual installation is possible. Download the ZIP file from Extension Repository, unzip and transfer it.
A directory should have been created "/system/modules/integrity_check".
Then call /contao/install.php - Perform Update Database.
Example of an Infection
How now looks like such a hack?
The attachment to the file index.php looked like this (shortened):
#c3284d# echo(gzinflate(base64_decode("ZZBNisMwDIX.......T7oD"))); #/c3284d#
Or like this (shortened):
<script type="text/javascript"> function frmAdd() { var ifrm = document.createElement('iframe'); .... }; window.onload = frmAdd; </script>
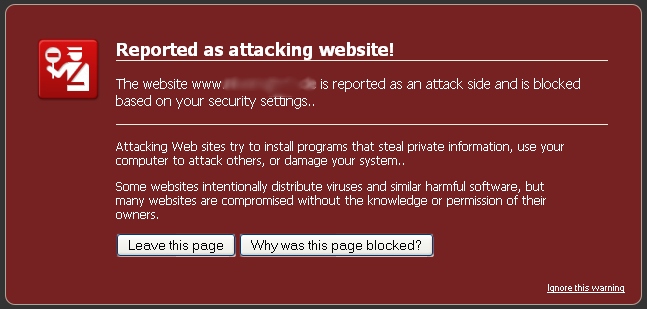
Site one the black list
When you does not react fast enough, and Google notices this, the page is set to the "black list". Browsers like Firefox use this to warn against unauthorized access to it. It looks like this:
Function of the module
In the current version, the most important PHP files are checked for modifications.
This files will be checked:
- index.php
- cron.php (from version 1.1.0)
- contao/index.php
- contao/main.php
- .htaccess (from version 3.1.0)
Special warning tests:
- Check for new Contao versions (from version 3.4.0)
- Check for install tool locking (from version 3.4.0)
Time of verification
This test is performed automatically (Contao-Cron), see the section Technical Details.
Detection
The check is identical to the official Contao check tool, that means via MD5 checksums. Checksums are available for comparison for Contao from 2.10.0.
From version 1.1.0, check via timestamps is possible.
Using
In the backend, you can see the results: System - System Log. Normally if everything is OK, no message appears. In its own module debug mode then there is only a message::
- Checking files for integrity is completed.
If modifications were detected, a message is generated for each file:
- Integrity status for file index.php is: Corrupt [MD5]
- Integrity status for cron.php file is corrupted [Timestamp]
- It was checked by time stamp, possible from version 1.1.0.
An information is available via System Log and mail, see the section Technical Details.
Technical Details
Creating integrity check
The integrity check need a check plan. This can be used for any of the files for the time, the art of check and the action.
Time intervals
- in Contao 2.10: daily, weekly, monthly
- in Contao 2.11: hourly, daily, weekly, monthly
- in Contao 3.0: minutely(manual), hourly, daily, weekly, monthly
Art of check
The detection of a change in the file is possible via:
- MD5 checksum
- Timestamps
Action
- System log: Message in the system log (backend)
- Mail to Admin: a mail is sent to the admin of the Contao installation.
- It will then creates also automatically an entry in the System log (from version 1.1.0)
Notes
System-Log und Mail
From version 1.1.0 automatically gets an entry in the system log when a mail is sent.
In Version 1.0.0, if you want to have both types of information, you creates the check twice, each with one of the actions:
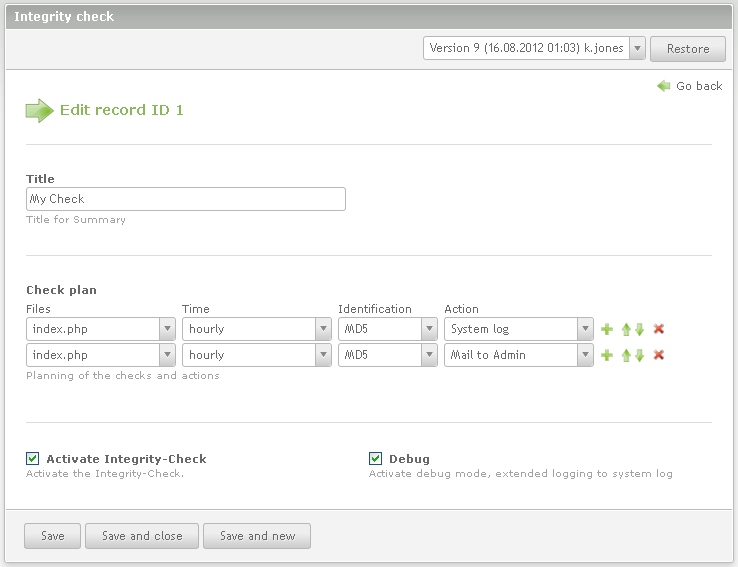
Here is an example only for the index.php. This is of course also for the other files.
There can be only one!
It is possible in the integrity check overview to create multiple checks. It basically makes no sense. Therefore, it is ensured that there can be only an integrity check, which is activated. If you switch a new integrity check active, all other existing tests are automatically switched inactive.
Protection against infection
Well, a general protection is probably not possible.
But there is a possibility that the malicious code is not executed. There is a ticket to GitHub, it is accepted for Contao 3. Here is the short info for Contao 2.
Edit the index.php, go to the method "run" in the last line, should be the line of 269th (2.11.5) Before the curly bracket insert an exit; or insert a row for it. Here is from line 268 as an example:
} }
change to:
} exit; }
Note: Now, the Integrity Check Tool as well as the Contao Check Tool report a change. Use the check vie timestamp now.